S1Box runs inside our dedicated deception cloud. You simply point traffic to your assigned traps and gain visibility into probing, scanning and malicious behavior — without touching production systems.
What S1Box builds.
Three types of deception traps designed to capture unauthorized activity and give you real signal.
Data Mirage
A high-fidelity simulation of internal systems designed to attract unauthorized exploration and capture meaningful signals about attacker intent.
Chameleon API
A dynamic API decoy that mimics modern cloud services and adapts to probing behavior — ideal for detecting reconnaissance and API enumeration techniques.
Spectre Shell
A controlled shell environment that safely records command-level activity, revealing how attackers behave when they believe they have gained a foothold.
Our approach.
Offensive thinking, defensive outcomes.
Traditional security focuses on blocking attacks. S1Box focuses on understanding them.
Decoys instead of blind spots.
Traps give attackers something to interact with — and give you clarity into what they're doing.
Privacy-first by design.
All intelligence comes solely from decoy interactions. No production traffic is ever analyzed.
Built by a small team obsessed with practicality.
Focused, fast, and engineered to deliver clear signal instead of noise.
S1Box is built by a small team that combines development, infrastructure, and offensive security thinking. We build tools we'd actually use in our own infrastructure — practical, privacy-respecting, and designed to give you real signal about who's probing your systems.
Think less enterprise compliance, more tactical advantage.
More than traps. An intelligence layer.
S1Box reveals how attackers behave when they think nobody is watching — origin, intent, tooling, and depth of engagement.
Adversary Origin Insight
Understand where malicious activity originates — region, network type and infrastructure profile — without inspecting production traffic.
Human vs Automation Detection
Differentiate opportunistic bots from meaningful operator-driven activity through timing and interaction patterns.
Tooling & Technique Indicators
Identify patterns associated with scanners, offensive frameworks, and scripted attacks.
Engagement Depth Score
Measure how deeply an attacker interacts with your decoy — a strong signal of their intent.
All intelligence is derived from decoy traffic only. No production data is ever analyzed.
See inside S1Box
A focused console for traps, activity, and attacker intelligence — so you know exactly what you're getting before you plug it in.
High-level view of your deception footprint and recent activity.
Dashboard preview
See how traps, telemetry, and threat signals land in the S1Box dashboard — all rendered inside our hosted device view.
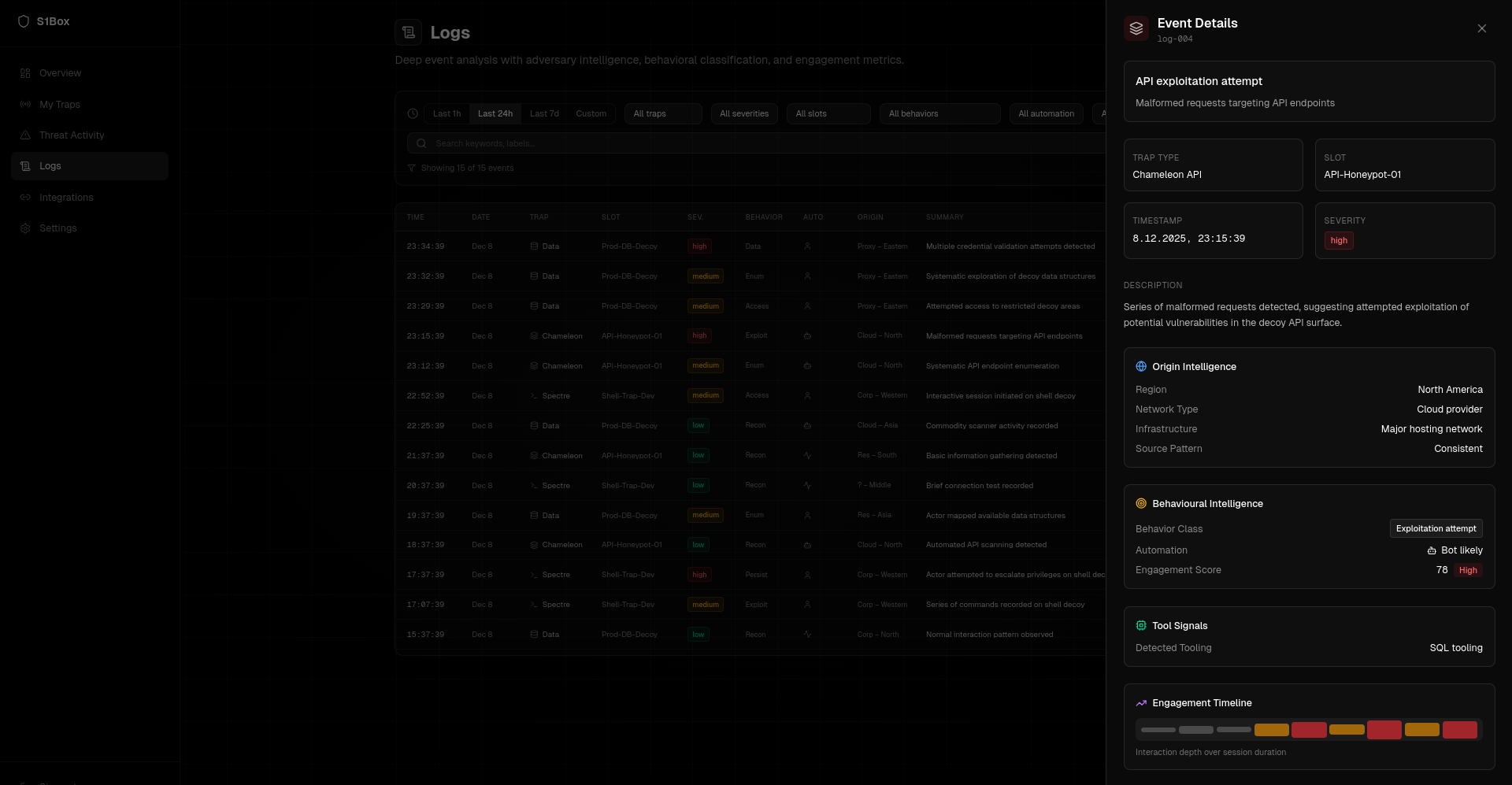
Inside S1BOX
Advanced security features and intelligence engines powering the S1BOX platform.
s1box@cloud:~$s1box@cloud:~$✔ Chameleon API: SSRF detection, internal enum, token bruteforce trackings1box@cloud:~$✔ SpecterShell SSH: recon/download/persistence command classifications1box@cloud:~$✔ Telemetry: threat_score, automation_score, rate_limit, confidence scoress1box@cloud:~$✔ HTTP fingerprinting: header order, UA patterns, bot/human hintss1box@cloud:~$✔ Deception Intel Engine: severity escalation, automation flag, engagementSimple, transparent pricing.
No hidden fees. No long contracts. Just slots and access.
Starter
1 slot
- Access to all 3 trap types
- Real-time threat telemetry
- Unified activity dashboard
- Privacy-first token access
- Best for validating deception on a single exposure point
- Placeholder
Team
3 slots
- Access to all 3 trap types
- Real-time threat telemetry
- Unified activity dashboard
- Privacy-first token access
- Run multiple traps in parallel for broader visibility
- Designed for small security teams
Ops
5 slots
- Access to all 3 trap types
- Real-time threat telemetry
- Unified activity dashboard
- Privacy-first token access
- Coverage across multiple environments
- Priority onboarding & guidance
Frequently asked questions.
Everything you need to know about slots and traps.